File Transfer Protocol (FTP) is a TCP protocol for downloading files between computers. In the past, it has also been used for uploading but, as that method does not use encryption, user credentials as well as data transferred in the clear and are easily intercepted.
常见FTP服务器软件
apt-cache show ftpd vsftpd proftpd-basic pure-ftpd | grep -A 5 Description-en
# ftpd: File Transfer Protocol (FTP) server This is the netkit ftp server. You are recommended to use one of its alternatives, such as vsftpd, proftpd, or pure-ftpd
# vsftpd: lightweight, efficient FTP server written for security This package provides the "Very Secure FTP Daemon", written from the ground up with security in mind.
# proftpd: Versatile, virtual-hosting FTP daemon - binaries ProFTPD is a powerful modular FTP/SFTP/FTPS server
# pure-ftpd: Secure and efficient FTP server Free, secure, production-quality and standard-conformant FTP server.比较&选择?
Google: ftpd vsftpd proftpd pure-ftpd comparison
一些可供参考的评价因素:
请自行根据以下任务需求从以上FTP服务器软件中选择一款满足所有任务要求的FTP服务器进行安装配置实验
to be continued …
resumed
NFS允许系统将其目录和文件共享给网络上的其他系统。通过NFS,用户和应用程序可以像访问本地文件一样访问远程系统上的文件。
to be continued …
resumed

The Server Message Block (SMB) Protocol is a network file sharing protocol, and as implemented in Microsoft Windows is known as Microsoft SMB Protocol. The set of message packets that defines a particular version of the protocol is called a dialect. The Common Internet File System (CIFS) Protocol is a dialect of SMB. Both SMB and CIFS are also available on VMS, several versions of Unix, and other operating systems.
CIFS协议是SMB协议的一个本地化实现(dialect,直译为“方言”),协议设计的初衷是文件共享,但微软的SMB协议还提供了一些额外功能:
某些数据报文会分组打包在一次数据传输中以降低响应延迟和提高带宽利用率,这种方法被称为“批处理”。
# 安装Samba服务器
sudo apt-get install samba
# 创建Samba共享专用的用户
sudo useradd -M -s /sbin/nologin demoUser
sudo groupadd demoGroup
sudo usermod -a -G demoGroup demoUser
sudo passwd demoUser
# 创建的用户必须有一个同名的Linux用户,密码是独立的
sudo smbpasswd -a cuc
# 创建测试用共享目录
sudo mkdir -p /srv/samba/demo
sudo chown -R demoUser:demoGroup /srv/samba/demo# 在/etc/samba/smb.conf 文件尾部追加以下“共享目录”配置
[demo]
path = /srv/samba/demo/
read only = no
guest ok = no
force create mode = 0660
force directory mode = 2770
force user = demoUser
force group = demoGroup
# Forced Parameters 可以强制所有连接共享目录的用户创建的文件、目录使用特定的权限位设定、属主用户和属主组(有安全风险)sudo apt-get install smbclient
# 查看远程 SMB 共享服务的共享目录清单
# Linux 搭建的 SMB 共享服务
smbclient -L 192.168.56.193 -U demoUser
# Enter WORKGROUP\demoUser's password:
#
# Sharename Type Comment
# --------- ---- -------
# print$ Disk Printer Drivers
# demo Disk
# IPC$ IPC IPC Service (cuc-lab server (Samba, Ubuntu))
# SMB1 disabled -- no workgroup available
# Windows 搭建的 SMB 共享服务
smbclient -L 192.168.56.182 -U demo
# Enter WORKGROUP\demo's password:
#
# Sharename Type Comment
# --------- ---- -------
# anon_share Disk
# IPC$ IPC 远程 IPC
# smb_share Disk
# SMB1 disabled -- no workgroup available
# 连接指定共享目录
smbclient //192.168.56.193/demo -U cuc
# 输入密码
# 下载整个文件夹
tarmode
recurse
prompt
## 下载指定目录 target_dir
mget target_dir
## 下载所有目录和文件
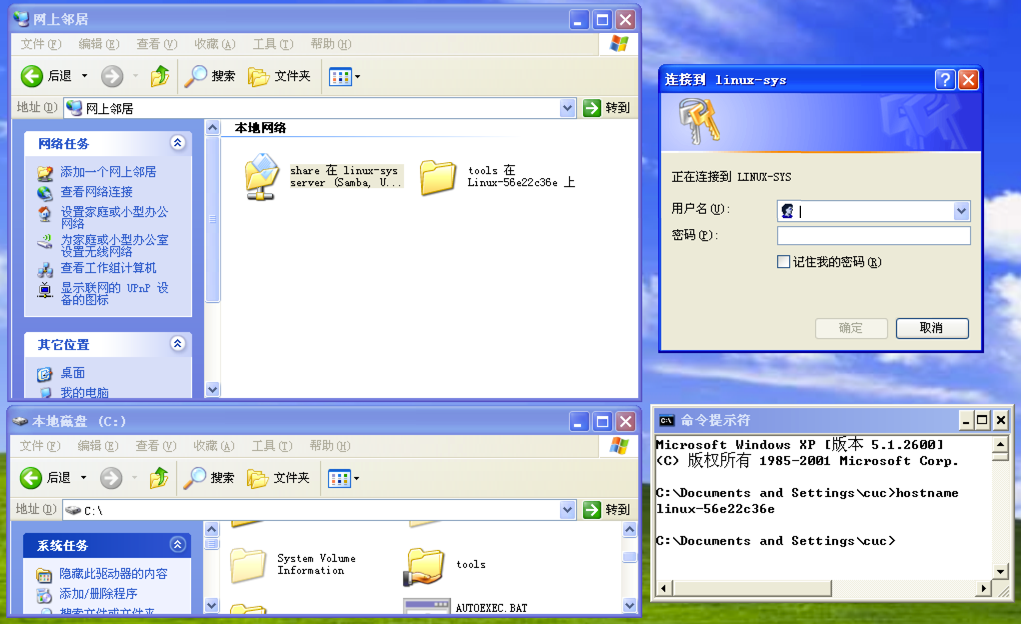
mget *开始菜单 –> gpedit.msc –>
Windows 设置 –> 安全设置 –>
网络列表管理器策略 –> 无法识别的网络
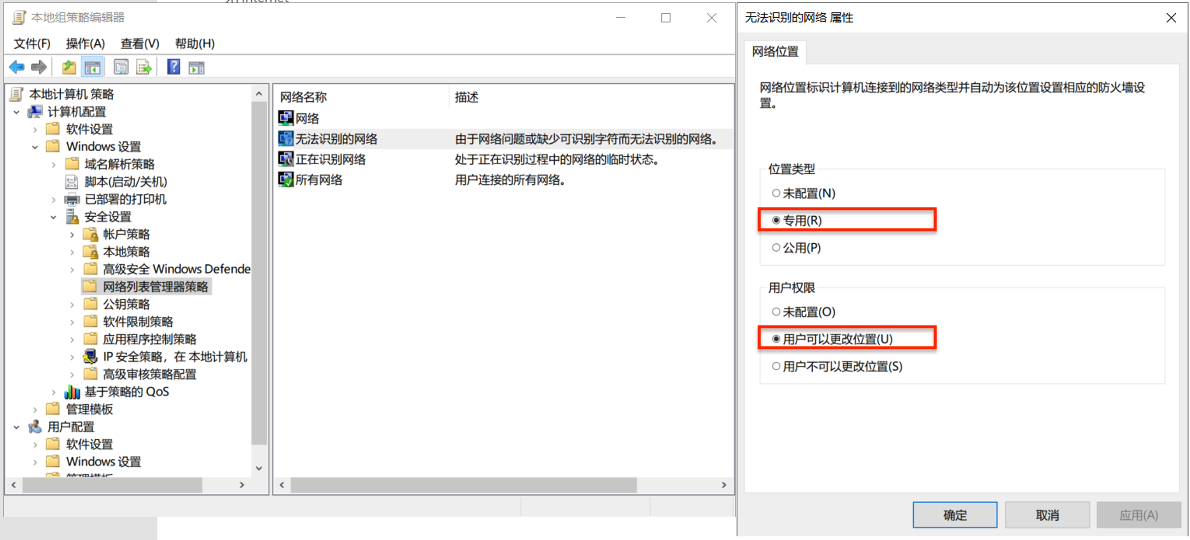
# 在 Windows CMD 中输入以下命令完成用户添加与口令设置
# 添加用户 demo 密码为 pass 用于访问共享文件夹
net user demo pass /ADD
# 实验完毕 删除用户
net user demo /DELETEput 只支持上传 当前目录下 文件! 命令前缀执行本地
shell 命令smb: \> ls
# . D 0 Thu Apr 22 05:38:17 2021
# .. D 0 Thu Apr 22 05:38:17 2021
# upload_demo A 12 Fri Apr 16 03:16:19 2021
# 新建文件夹 D 0 Thu Apr 22 06:57:22 2021
#
# 33405695 blocks of size 4096. 21963037 blocks available
smb: \> !ls -la
# total 52
# drwxr-xr-x 6 cuc cuc 4096 Apr 22 23:09 .
# drwxr-xr-x 3 root root 4096 Feb 20 11:21 ..
# drwx------ 3 cuc cuc 4096 Apr 12 01:31 .ansible
# -rw------- 1 cuc cuc 2472 Apr 22 07:53 .bash_history
# -rw-r--r-- 1 cuc cuc 220 Feb 25 2020 .bash_logout
# -rw-r--r-- 1 cuc cuc 3789 Apr 12 06:40 .bashrc
# drwx------ 2 cuc cuc 4096 Feb 20 11:43 .cache
# -rw------- 1 cuc cuc 39 Apr 22 06:33 .lesshst
# -rw-r--r-- 1 cuc cuc 807 Feb 25 2020 .profile
# drwx------ 2 cuc cuc 4096 Apr 12 01:31 .ssh
# -rw-r--r-- 1 cuc cuc 0 Feb 20 11:44 .sudo_as_admin_successful
# -rw-rw-r-- 1 cuc cuc 0 Apr 22 23:09 test
# -rw-rw-r-- 1 cuc cuc 12 Apr 22 06:02 upload_demo
# -rw------- 1 cuc cuc 867 Apr 22 06:18 .viminfo
# drwxrwxr-x 3 cuc cuc 4096 Apr 22 06:57 新建文件夹
smb: \> help lcd
# HELP lcd:
# [directory] change/report the local current working directory# Linux 宿主机
ls -ld /srv/samba/demo/
# drwxr-xr-x 2 demoUser demoGroup 4096 Apr 22 05:35 /srv/samba/demo/
# Windows 宿主机OpenSSH Server
OpenSSH Server 开机自启动# 以下代码需要在「管理员权限」的 PowerShell 中执行
Start-Service sshd
# OPTIONAL but recommended:
Set-Service -Name sshd -StartupType 'Automatic'
# Confirm the firewall rule is configured. It should be created automatically by setup.
Get-NetFirewallRule -Name *ssh*
# There should be a firewall rule named "OpenSSH-Server-In-TCP", which should be enabled
# If the firewall does not exist, create one
New-NetFirewallRule -Name sshd -DisplayName 'OpenSSH Server (sshd)' -Enabled True -Direction Inbound -Protocol TCP -Action Allow -LocalPort 22PowerShell# 以下代码需要在「管理员权限」的 PowerShell 中执行
New-ItemProperty -Path "HKLM:\SOFTWARE\OpenSSH" -Name DefaultShell -Value "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -PropertyType String -Force# 不能使用 ssh-copy-id
# 在「管理员权限」的 powershell 中执行以下命令
cd $ENV:PROGRAMDATA/ssh
New-Item -ItemType file administrators_authorized_keys
# 将公钥指纹信息写入上述新创建的 administrators_authorized_keys
# 请自行替换以下 <> 内的公钥指纹信息
# 这里的 -encoding ascii 非常重要,因为默认不使用该参数时
# Out-File 写入的文本是双字节编码且使用了 BOM 文件头
echo '<content-of-id_rsa.pub>' | Out-File -encoding ascii administrators_authorized_keys
# 检查自己使用的 PowerShell 版本
# $PSVersionTable
# Name Value
# ---- -----
# PSVersion 5.1.19041.906
# PSEdition Desktop
# PSCompatibleVersions {1.0, 2.0, 3.0, 4.0...}
# BuildVersion 10.0.19041.906
# CLRVersion 4.0.30319.42000
# WSManStackVersion 3.0
# PSRemotingProtocolVersion 2.3
# SerializationVersion 1.1.0.1
# ref: https://docs.microsoft.com/en-us/powershell/module/microsoft.powershell.utility/out-file?view=powershell-5.1
# 5.1 版 Powershell 使用 Out-File 写入文件时所有多字节编码方式均用到了 BOM 头
# ref: https://docs.microsoft.com/en-us/powershell/module/microsoft.powershell.utility/out-file?view=powershell-7
# 7.0+ 版 Powershell 提供了 utf8NoBOM 编码方式
# 配置上述 administrators_authorized_keys 正确的属主和访问权限
$acl = Get-Acl $ENV:PROGRAMDATA\ssh\administrators_authorized_keys
$acl.SetAccessRuleProtection($true, $false)
$administratorsRule = New-Object system.security.accesscontrol.filesystemaccessrule("Administrators","FullControl","Allow")
$systemRule = New-Object system.security.accesscontrol.filesystemaccessrule("SYSTEM","FullControl","Allow")
$acl.SetAccessRule($administratorsRule)
$acl.SetAccessRule($systemRule)
$acl | Set-Acl
# 检查 administrators_authorized_keys 文件的权限设置
# Access 一项只能且必须只有
# Access : NT AUTHORITY\SYSTEM Allow FullControl
# BUILTIN\Administrators Allow FullControl
get-acl .\administrators_authorized_keys | fl
# Path : Microsoft.PowerShell.Core\FileSystem::C:\ProgramData\ssh\administrators_authorized_keys
# Owner : BUILTIN\Administrators
# Group : DESKTOP-HQOR9HG\None
# Access : NT AUTHORITY\SYSTEM Allow FullControl
# BUILTIN\Administrators Allow FullControl
# Audit :
# Sddl : O:BAG:S-1-5-21-3489025807-4051503630-1690866609-513D:PAI(A;;FA;;;SY)(A;;FA;;;BA)# 注意 Windows 路径分隔符要使用 / 而不是 \
scp demo@192.168.56.182:c:/programdata/ssh/administrators_authorized_keys ./